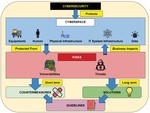
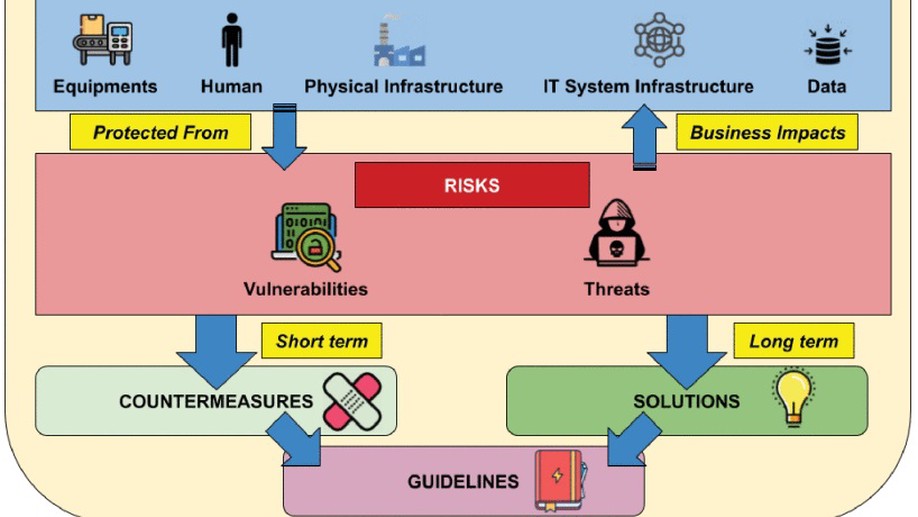
Industry 4.0 is a revolution in manufacturing by introducing disruptive technologies such as Internet of Things (IoT) and cloud-computing into the heart of the factory. The resulting increased automation and the improved production synergy between stocks, supply chains and customer demands, come along with the threats and attacks from the Internet. Despite extensive literature on the cybersecurity topic, many actors in manufacturing factories are just realizing the impact of cybersecurity in the preservation of their business. This paper introduces step-by-step the concepts and practical aspects of an Industry 4.0 manufacturing factory that are related to cybersecurity. Based on a subdivision of a typical factory into several generic perimeters, we present the vulnerabilities and threats regarding the network and devices usually found in each perimeter. Therefore, it is more efficient to present the recent proposals of the literature regarding cybersecurity guidelines and solutions in Industry 4.0. Instead of spreading a lot of references regarding every aspect of cybersecurity, we focused on a limited number of papers among the recent references. However, for each paper, we provide the details about the purpose of the proposal, the methodology adopted, the technical solution developed and its evaluation by the authors. These solutions range from classical cybersecurity countermeasures to innovative ones, such as those based on honeypots and digital twins. In order to deliver a review also useful to non scientists, we present our guidelines along with those of some organizations involved in cybersecurity harmonization and standardization in the world.